Posts Tagged ‘Best Practice’
NUI Galway Data Breach – Lessons learned?
The NUI Galway data breach that was revealed this week is concerning. Particularly the initial reports about the breach, which weren’t very clear.
Read MoreVulnerable Shopping Carts lead to Credit Card breaches
You may have heard about the Ticketmaster data breach earlier this summer. You probably also have heard about the British Airways data breach at the start of this month. A new breach at another large online marketplace using the same technique shows that vulnerable shopping carts are being exploited more and more.
Read MoreEir laptop theft – could have been worse
The eir laptop theft that was revealed this week was pretty … actually … it was really bad and deeply embarrassing for eir. However details that emerged from the statement by the Data Protection Commission showed that it could have been a LOT worse. 1,500 Laptops worse!
Read MoreWill your website be marked “Not Secure”?
Starting next week, some websites will be marked “Not Secure”. This is because the Chrome browser will no longer be highlighting secure websites, but will instead highlight insecure websites.
Read MoreIs somebody else using your password?
Is somebody else using your password? If your password is “123456”, then absolutely yes. Nearly 21 million other accounts use that same password. But how about “Gobbledegook”? That password is actually used by at least 9 other accounts. “LiamIsANiceHelpfulCyberSecurityPerson” has not been used before – I might use it for myself. ?
Read MoreVulnerable Cisco Firewalls
It emerged last week that a security researcher had made a very significant discovery, which showed that popular firewalls made by Cisco had a vulnerability that was scored a perfect 10 out of 10 on the CVSS (Common Vulnerability Scoring System) scale.
Read MoreSimple Security Planner tool for EVERYONE!
I love it when I get to tell people about another great security tool. This simple Security Planner tool is another FREE resource that can really help protect you, your loved ones, your friends and co-workers.
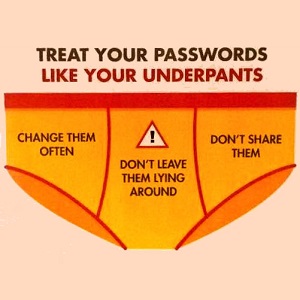
Read MorePassword Sharing = Data Breach
I saw the tweet below about password sharing from Nadine Dorries, currently a British MP and initially thought “That’s not a good idea. This person needs to receive some security awareness training.” I even have a commandment for it.
Read MoreQuad9 – Safer addressing on the internet
I sometimes grow weary of the never ending stories of the bad guys being successful. Quad9 is a free Domain Name Service (DNS) from the good guys that should make life safer for everyone.
Read MoreDouble check your security.
There is an easy double check that you can implement which will offer you excellent protection. It is called two factor authentication (or two step verification).
Read MoreWhat Ophelia taught me about power.
Hurricane Ophelia came to Ireland this week and caused quite a lot of damage across the country. Trees were blown down. Roofs were ripped off. The electrical power supply grid was widely disrupted. The area where my office is, had no power for over 48 hours.
Read MoreCloud Security is your responsibility.
I see a read a lot of cyber security stories and nothing surprises me any more. I constantly see stories about breaches and phishing. Now I turn my jaundiced eye on cloud security.
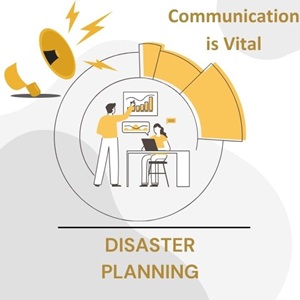
Read MoreCommunication is vital after a disaster.
Maersk Line were one of the biggest victims of the Petya/NotPetya Ransomware worm that struck on 27th June 2017. Here are some details, in case you missed it. Two weeks later, they are still not back to full operational capacity, but they are doing something really well. The are using the critical competence of communication…
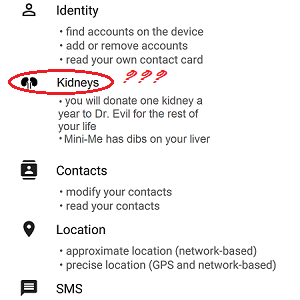
Read MorePermission to spy on you?
Most people have smart phones these days and of course smart phones really come into their own through the use of Apps. There seems to be an app for every conceivable thing and lots of them are free. The phone makers make a good effort to protect us from bad apps by making sure that…
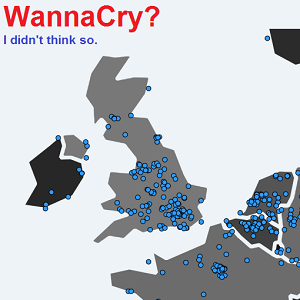
Read MoreDo you WannaCry? I didn’t think so.
I delayed this week’s blog, just to let some of the dust settle on the whole WannaCry (also known as WCry or WannaCrypt) furore and see if we can learn anything from it that will help protect my readers going forward. I’ll start with some easy background on Ransomware and them explain what was special…
Read More