Posts Tagged ‘Defence in Depth’
How to deal with Ransomware.
I want to come back to this topic on how to deal with Ransomware. This is because I keep meeting business people in the training that I deliver who, either know of somebody or have themselves, suffered a Ransomware incident.
Read MoreVulnerable Shopping Carts lead to Credit Card breaches
You may have heard about the Ticketmaster data breach earlier this summer. You probably also have heard about the British Airways data breach at the start of this month. A new breach at another large online marketplace using the same technique shows that vulnerable shopping carts are being exploited more and more.
Read MorePosh POS was Compromised
A headline worthy of The Register and I’m surprised they didn’t grab it. So what POS was compromised? Well none other than Saks Fifth Avenue, Saks Off Fifth and Lord & Taylor.
Read MoreSimple Security Planner tool for EVERYONE!
I love it when I get to tell people about another great security tool. This simple Security Planner tool is another FREE resource that can really help protect you, your loved ones, your friends and co-workers.
Read MoreQuad9 – Safer addressing on the internet
I sometimes grow weary of the never ending stories of the bad guys being successful. Quad9 is a free Domain Name Service (DNS) from the good guys that should make life safer for everyone.
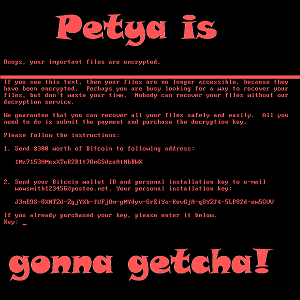
Read MoreThe latest Ransomware outbreak – Petya
So here we go again with another outbreak of Ransomware, based on the National Security Agency (NSA) hacking tools that were leaked by a hacking group. Some experts are calling this one Petya, as it seems very similar to the Petya Ransomware strain that has been around for over a year.
Read MoreDo you WannaCry? I didn’t think so.
I delayed this week’s blog, just to let some of the dust settle on the whole WannaCry (also known as WCry or WannaCrypt) furore and see if we can learn anything from it that will help protect my readers going forward. I’ll start with some easy background on Ransomware and them explain what was special…
Read MoreTake a 2-Minute Privacy check-up.
After last week’s brief shenanigans with GMail getting phished badly and the recommendation I made about how to help correct and protect yourself from that nasty piece of work, I went ahead and did something I had not done in some time. A privacy check-up and there is also a security or account check-up available too.
Read MoreProtect your on-line accounts, but not with text messages.
As I outlined here, if you are using on-line accounts for e-mail, social media, etc. then one of the strongest means of protecting yourself from the evil doers is to use, what is called, two factor authentication. If you are not doing this now, you really should be as it improves your protection massively. This is…
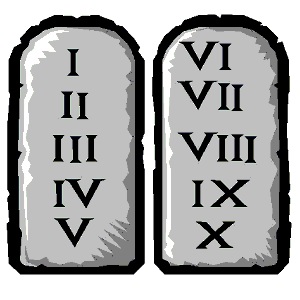
Read MoreThe Ten Commandments of Cyber Security
The Ten Commandments of Cyber Security Click on the links for a summary and detail of each commandment.
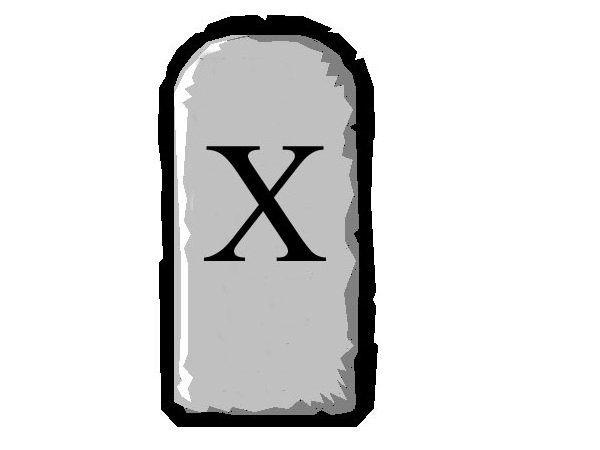
Read MoreX. Thou shalt only use the official app store for apps.
Summary: This commandment is more targeted at the mobile device side of technology, but app stores are spreading into the desktop/laptop areas by way of Windows Store for Windows 8.1 and Windows 10. From a mobile device perspective, you should only use the official app store for that platform. Most smartphones come with a setting…
Read MoreIX. Thou shalt never insert nor allow to be inserted, a USB memory stick that thy hath never had complete control of since it was removed from its packaging.
Summary: This is an easy commandment to follow, but there might be temptation to breach it for convenience. If you find a USB memory stick on the street or in a car park, bring it to a waste electrical goods recycling centre and dispose of it there. I was going to say place it in…
Read MoreVIII. Thou shalt never reveal thine password for any account to anyone.
Summary: This is one that should be an absolute no-brainer. Your password is your key to your data and applications. It should be absolutely sacrosanct and known only to yourself and NOBODY else. Nobody else has a need for it, except the evil doers and you wouldn’t give it to them willingly, would you? It…
Read MoreVII. Thou shalt use two factor authentication on any account that provides the facility.
Summary: What is two factor authentication? Put simply it is a way of gaining access to an application by using two means of verifying the identity of the person requesting access. Typically the means of verification are (a) something you know – e.g.- a Password (b) something you have – e.g.- a Mobile phone (c)…
Read MoreVI. Thou shalt encrypt all data stored on thine mobile devices.
Summary: Your data is valuable to you. Even something as simple as the phone numbers in your phone’s contact app. It’s also valuable to the evil doers. They would dearly love access to your phone with all of the valuable e-mail, SMS, call logs, WhatsApp messages. Everything on your phone will be of some use…
Read More