Posts Tagged ‘Phishing’
#WeekendWisdom 091 Phishing for Credentials
Welcome to #WeekendWisdom number 91. This week we’re going to talk about phishing for credentials.
Read More#WeekendWisdom 062 Email Thread Hijacking
Welcome to #WeekendWisdom number 62. This week we’re going to talk about Email Thread Hijacking.
Read MoreNot GDPR Compliant – Really?
A colleague at another company forwarded me an email he’d received knowing that I’d get a kick out of it. It claimed to be from the UK GDPR Compliance Directory and that his company was not GDPR compliant. Of course no such directory exists and this was nothing but a ruse.
Read MoreHow to deal with Ransomware.
I want to come back to this topic on how to deal with Ransomware. This is because I keep meeting business people in the training that I deliver who, either know of somebody or have themselves, suffered a Ransomware incident.
Read MoreSextortion scam – a follow up.
This time last month I posted about a sextortion scam that was sending out large amounts of emails to people claiming to have recorded them watching porn. As proof that they meant business, they included an old password the victim had previously used. There have been some developments.
Read MoreA Sextortion Scam
The evil doers have launched a new sextortion scam on the internet. This one is interesting to say the least as it does use a technique to sucker you into believing it is real, without giving you any actual evidence of what they allege to have on you.
Read MoreSneaky Tax Refund e-mails
Tax refund scam e-mails are nothing new. They’ve been doing the rounds for many many years at this stage. Like the “Nigerian Prince” scams, that are enjoying a resurgence presently, the tax refund scams might catch out those who are new to the internet and may not have heard of such scams before.
Read MoreDodgy e-mail that looks legit.
I received a dodgy e-mail on my personal account yesterday. I’m surprised the GMail spam filters didn’t catch it and flag it for me. Like last weeks story, this message looked kinda plausible.
Read MoreDouble check your security.
There is an easy double check that you can implement which will offer you excellent protection. It is called two factor authentication (or two step verification).
Read MoreMalicious e-mail from Yahoo! breach.
I’ve received the first malicious e-mail as a result of a compromised Yahoo! e-mail account. I’ve warned the individual and hopefully he still has control of the account and can secure it again.
Read MoreYahoo breach – Round 3 … Billion! ?
If you had a Yahoo!, BT or Sky e-mail account (also AT&T, Frontier.com and Rogers) back in 2013, well you are definitely part of the latest and greatest Yahoo breach.
Read MorePhishing subject lines – Top 10.
What would you expect if you got an e-mail with the subject line of “Security Alert”? How about “Unusual sign-in activity”? You probably expect it to be an e-mail that is trying to raise your awareness about some potential security issue. I’m afraid it is likely not. These are just two examples from the Top…
Read MorePhone scams – some current examples
In the last few days, I’ve received a couple of attempted phone scams. The first was a new one on me, but the second was an old favourite.
Read MoreHow a typo can cause you problems.
Nobody is perfect and we all make mistakes. One of the most common mistakes, in particular with mobile phones and their small keyboards, is the simple typo. Did you know that the evil doers have got sneaky ways that they try to capitalise on your fumbling fingers? It’s a technique called “Typosquatting“.
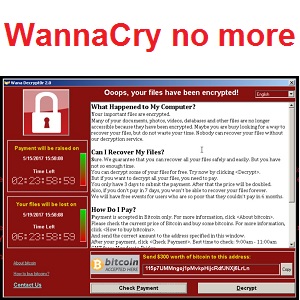
Read MoreWannaCry no more. At least for now.
I’m just going to have a short article this week, just to close off the WannaCry story and counter any of the misinformation that was spread by some supposed “experts”. WannaCry is still circulating and affecting machines, but thanks to the kill switch discovered by @MalwareTechBlog, it is more or less neutralised now. Those machines still…
Read More