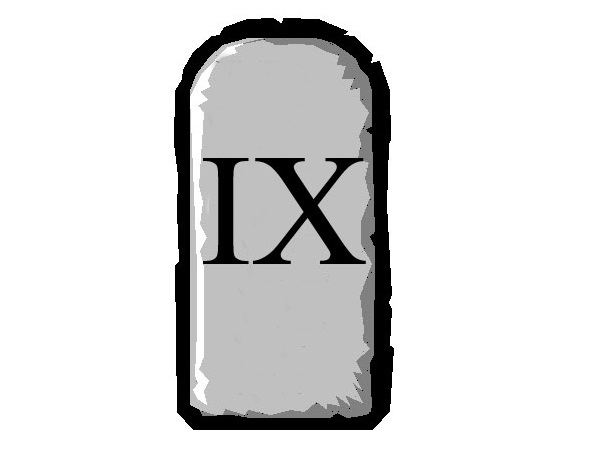Posts Tagged ‘Security’
Yahoo! tries for new world record and wins … but it already had the world record!
You all heard the headlines during the year about the massive Yahoo! hack, where in late 2014, hackers had stolen the names, addresses, mobile telephone numbers, dates of birth, security questions and passwords of 500+ million accounts. This was a new world record for the amount of user accounts stolen on the internet. Well bless…
Read MoreDo you own a Netgear router? If so, you may have a serious vulnerability.
If you have one of the following Netgear router models, you could be exposed to a serious vulnerability: R6250 R6400 R6700 R7000 R7100LG R7300 R7900 R8000
Read MoreThere is a lot of variations in scam e-mail the last couple of days.
I yearn for the days when evil e-mail was so easily identified “becuse it wuz ritten in, gud, inglish wit grate spellhng an pun.tation”. ? In the last couple of days, the evil doers have been varying their scam e-mails fairly wildly and it’s bound to catch out some people. I’ll run through three sneaky methods…
Read MoreThe Internet of Evil Things continues to grow.
The first time I saw that picture of the Dr. Evil meme, I never thought that it might be possible for the numbers to reach those nonsensical values, but if Internet connected brooms are in our future (see below), we might be in serious trouble, if the manufacturers of such devices keep ignoring the need…
Read MoreDetails emerge about the huge internet attack last Friday.
I’m sure you’ve all heard about the internet attack in the US last Friday, where sites such as Twitter, Amazon, Spotify, PayPal and Netflix (amongst others) were taken offline (effectively). This was done by what is called a Distributed Denial Of Service (DDOS) attack and it targeted a company called Dyn, which provides all of…
Read MoreSnail mail delivers USB keys … WTF?
I find I’m writing a second article about Evil USBs within a week. At least these ones don’t destroy your equipment, but they might infect you with nasty software that does things that you really wouldn’t want it doing. In this case, in Victoria, Australia, Evil Doers were dropping USB drives into people’s mailboxes. The…
Read MoreDon’t open that Voicemail!
The evil doers are up to their old tricks, trying to hoodwink people into opening up their dastardly files and execute their nasty contents. Usually they send files that claim to be invoices or bank statements, which will normally catch out a small percentage of their targeted group – accountants in this case, because accountants…
Read MoreEvil doers just being evil … news at 11!
The good folk over at Cisco’s Talos Threat Intelligence Organisation have been looking at a new piece of “apparent” Ransomware called Ranscam. The reason I use “apparent” is because it doesn’t hold any of your data to ransom, quite simply because it’s deleted it already! That doesn’t stop it trying to get you to pay…
Read MoreThe Ten Commandments of Cyber Security
The Ten Commandments of Cyber Security Click on the links for a summary and detail of each commandment.
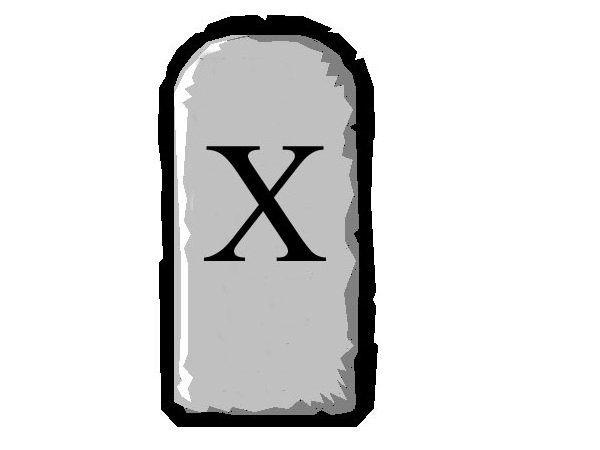
Read MoreX. Thou shalt only use the official app store for apps.
Summary: This commandment is more targeted at the mobile device side of technology, but app stores are spreading into the desktop/laptop areas by way of Windows Store for Windows 8.1 and Windows 10. From a mobile device perspective, you should only use the official app store for that platform. Most smartphones come with a setting…
Read MoreIX. Thou shalt never insert nor allow to be inserted, a USB memory stick that thy hath never had complete control of since it was removed from its packaging.
Summary: This is an easy commandment to follow, but there might be temptation to breach it for convenience. If you find a USB memory stick on the street or in a car park, bring it to a waste electrical goods recycling centre and dispose of it there. I was going to say place it in…
Read MoreVIII. Thou shalt never reveal thine password for any account to anyone.
Summary: This is one that should be an absolute no-brainer. Your password is your key to your data and applications. It should be absolutely sacrosanct and known only to yourself and NOBODY else. Nobody else has a need for it, except the evil doers and you wouldn’t give it to them willingly, would you? It…
Read MoreVII. Thou shalt use two factor authentication on any account that provides the facility.
Summary: What is two factor authentication? Put simply it is a way of gaining access to an application by using two means of verifying the identity of the person requesting access. Typically the means of verification are (a) something you know – e.g.- a Password (b) something you have – e.g.- a Mobile phone (c)…
Read MoreVI. Thou shalt encrypt all data stored on thine mobile devices.
Summary: Your data is valuable to you. Even something as simple as the phone numbers in your phone’s contact app. It’s also valuable to the evil doers. They would dearly love access to your phone with all of the valuable e-mail, SMS, call logs, WhatsApp messages. Everything on your phone will be of some use…
Read MoreV. Thou shalt cast aside e-mails from strangers and not open attachments/click links they may send you.
Summary: I’m going to start this summary with some scary figures. 93% of phishing e-mails in Quarter 1 2016 have carried a Ransomware payload (source – PhishMe Q1 2016 Malware review). 30% of people that receive phishing e-mails open them and 12% of those that do, then open attachments or click on links (source –…
Read More