There is a lot of variations in scam e-mail the last couple of days.
I yearn for the days when evil e-mail was so easily identified “becuse it wuz ritten in, gud, inglish wit grate spellhng an pun.tation”. ?
In the last couple of days, the evil doers have been varying their scam e-mails fairly wildly and it’s bound to catch out some people.
I’ll run through three sneaky methods that have been attempted on others over the last 48 hours.
(1) Non-Delivery Receipt.
You know these e-mails. You get them when you send an e-mail, but you make a mistake and send it to an address which doesn’t exist or the mailbox has a size limit and your e-mail breaches that limit. This is the text of the Non-Delivery Receipt (NDR) in this instance:
Your message was not delivered due to the following reason(s):
Your message could not be delivered because the destination server was
not reachable within the allowed queue period. The amount of time
a message is queued before it is returned depends on local configura-
tion parameters.
Most likely there is a network problem that prevented delivery, but
it is also possible that the computer is turned off, or does not
have a mail system running right now.
There is a ZIP file attached to the NDR, which of course has some nasty software that does not have your best interest at heart. ?
Just delete the scam e-mail.
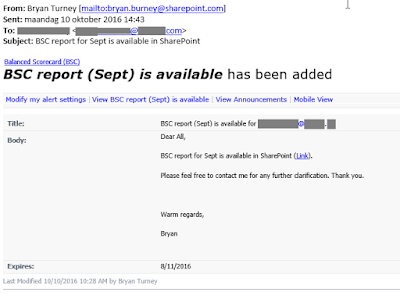
(2) A Microsoft Sharepoint Notification.
This is a particularly sneaky one, as lots of larger organisations depend on Sharepoint’s sharing abilities.
The e-mail looks something like this:
The Link in the body text would take you to a not particularly nice website. No doubt it might attempt to infect your computer. ?
Just delete the scam e-mail.
(3) Somewhat abusive attempt to get you to open the attachment.
Please be warned, there is a profanity ahead. I wanted to leave it in as it does generate something of a visceral reaction when you read it.
Subject: credit card charge from <your company’s domain name>
What is this fucking charge on my card?
I never visited or bought anything from <your company’s domain name>.
I have attached a screenshot of my statement.
I want my money back!!!
I have attached my card statement, please get back to me ASAP.
Thank you
company name
person name
phone
fax
There is a Word document attached to the e-mail, which of course has … nasty ransomware, which will scramble all of your files and leave you with a very bad day ahead. ?
Just delete the scam e-mail.
Conclusion
I hope you noticed that I was pretty consistent in my recommended action … this is because it is from Commandment #5 in our Ten Commandments of Cyber Security.
If you wish to train your staff on how they can spot these type of e-mails, then have a read of this course outline and contact us on the number or e-mail address at the end of that. We’ll be happy to discuss your training requirements and provide a quotation to cover same.
And lets be careful out there.
H/T to the SANS Institute’s Internet Storm Centre @ https://isc.sans.edu/