Posts Tagged ‘Security’
Simple Security Planner tool for EVERYONE!
I love it when I get to tell people about another great security tool. This simple Security Planner tool is another FREE resource that can really help protect you, your loved ones, your friends and co-workers.
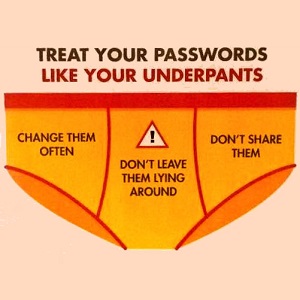
Read MorePassword Sharing = Data Breach
I saw the tweet below about password sharing from Nadine Dorries, currently a British MP and initially thought “That’s not a good idea. This person needs to receive some security awareness training.” I even have a commandment for it.
Read MoreQuad9 – Safer addressing on the internet
I sometimes grow weary of the never ending stories of the bad guys being successful. Quad9 is a free Domain Name Service (DNS) from the good guys that should make life safer for everyone.
Read MoreDouble check your security.
There is an easy double check that you can implement which will offer you excellent protection. It is called two factor authentication (or two step verification).
Read MoreHeathrow’s dangerous data breach
You may not have heard about this, as it emerged on Sunday. There was a data breach relating to Heathrow Airport. A fully accessible USB memory stick was found on a London street.
Read MoreMalicious e-mail from Yahoo! breach.
I’ve received the first malicious e-mail as a result of a compromised Yahoo! e-mail account. I’ve warned the individual and hopefully he still has control of the account and can secure it again.
Read MoreYahoo breach – Round 3 … Billion! ?
If you had a Yahoo!, BT or Sky e-mail account (also AT&T, Frontier.com and Rogers) back in 2013, well you are definitely part of the latest and greatest Yahoo breach.
Read MoreDeloitte breach is very embarrassing.
The Deloitte breach that was revealed by the Guardian last week was incredibly embarrassing for the firm. They have been named Gartner’s No. 1 Security Consultancy for 5 years in a row ?.
Read MoreCloud Security is your responsibility.
I see a read a lot of cyber security stories and nothing surprises me any more. I constantly see stories about breaches and phishing. Now I turn my jaundiced eye on cloud security.
Read MoreDraughty Backdoor in popular application.
It was revealed a couple of days ago that a widely used application had a backdoor in it. A specific version of CCleaner, a well known utility for doing housekeeping on computers, had been compromised by evil doers.
Read MorePacemaker updates – they’re a thing now!?!?
On August 23rd the Food and Drug Administration (FDA) in the US approved the deployment of a software update for pacemakers made by St. Jude Medical. This was to fix vulnerabilities discovered in 2016, which were patched by St. Jude Medical in January 2017. Actually, vulnerabilities in pacemakers have been around for quite a while,…
Read MoreData Breach Handling – 3 recent examples.
You might remember that last year, Yahoo! were shown to have suffered a data breach not once, but twice which led to the personal data associated with ~1.5 billion accounts being stolen by evil doers. This was a pretty massive story at the time and it was widely reported.
Read MoreCommunication is vital after a disaster.
Maersk Line were one of the biggest victims of the Petya/NotPetya Ransomware worm that struck on 27th June 2017. Here are some details, in case you missed it. Two weeks later, they are still not back to full operational capacity, but they are doing something really well. The are using the critical competence of communication…
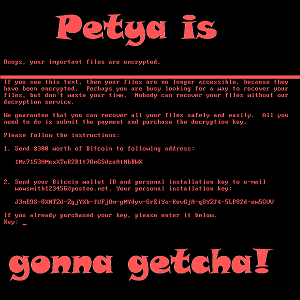
Read MoreThe latest Ransomware outbreak – Petya
So here we go again with another outbreak of Ransomware, based on the National Security Agency (NSA) hacking tools that were leaked by a hacking group. Some experts are calling this one Petya, as it seems very similar to the Petya Ransomware strain that has been around for over a year.
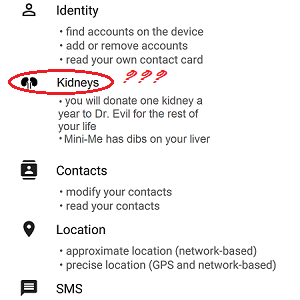
Read MorePermission to spy on you?
Most people have smart phones these days and of course smart phones really come into their own through the use of Apps. There seems to be an app for every conceivable thing and lots of them are free. The phone makers make a good effort to protect us from bad apps by making sure that…
Read More