The latest Ransomware outbreak – Petya
 So here we go again with another outbreak of Ransomware, based on the National Security Agency (NSA) hacking tools that were leaked by a hacking group. Some experts are calling this one Petya, as it seems very similar to the Petya Ransomware strain that has been around for over a year.
So here we go again with another outbreak of Ransomware, based on the National Security Agency (NSA) hacking tools that were leaked by a hacking group. Some experts are calling this one Petya, as it seems very similar to the Petya Ransomware strain that has been around for over a year.
Others are calling it NotPetya or Petna, because it is essentially a new form of Ransomware. Whatever it’s called, doesn’t matter except to journalists who need sexy headlines. This is a significant threat, particularly to businesses that have networks that span the globe. I’ll refer to it as Petya for the purpose of this post.
There is still a lot of uncertainty around this, with conflicting reports indicating it comes in via e-mail or that it worms its own way into people’s networks. The latter is probably the more correct in this case. However the vast majority of other Ransomware strains that are out there usually spread by e-mail. So, as always follow Commandment 5 and discard any email from strangers and be cautious of email from known sources.
There seems to be growing confidence that this emanated from an accounting application that is widely used in the Ukraine called MeDoc or M.E.Doc. It seems the creator of the application was compromised and the evil doers put the Ransomware into their application and then pushed it to all their customers via an automatic update.
Update as at 19:00 (IST) 28/06/2017:
As we mentioned earlier, it now seems that Microsoft have confirmed that the M.E.Doc application, widely used in Ukraine, was the initial source of the outbreak.
There are now reports emerging that a Ukrainian Government website is delivering or attempting to deliver Petya Ransomware to any visitors to the site. This is known as a Watering hole attack. If this starts spreading to other sites, this would become much more serious. Follow us on either/both Facebook and Twitter to be kept up to date.
Should I be worried?
If you took action to protect yourself from WannaCry by patching all of your systems with the March updates from Microsoft, you are in pretty good shape. (Apologies for the tech-jargon in the next sentence – you might want to ask your IT provider about this) If the SMBv1 protocol (a means of accessing file shares across a network) through your firewalls has been closed or simply disabled any SMBv1 services running on your PC or servers, then it currently seems that Petya will not be able to get inside your network.
HOWEVER if you have ONE machine that has NOT been patched with the MARCH updates, then you may be at grave risk. This Petya strain of Ransomware, once it compromises a machine by exploiting the vulnerability patched in March, appears to use other methods to access the remaining machines within your network, even ones that are currently full patched.
So please, follow Commandment 1 and keep your machines fully patched as soon as is practical after the patches are released.
How do I know if I’m being affected?
If Petya gets into your machine, you may not immediately realise it, because the first thing it seems to do is schedule a reboot for 1 hour after it infects you. It is unclear as to whether it starts looking to reach other machines in your network at this time or after the reboot. I would suspect it probably would be trying to infect other machines in your network at this stage.
If your machine suddenly reboots without notice and starts up like this POWER OFF the machine immediately (pull the plug or press and hold the power button until it shuts down):
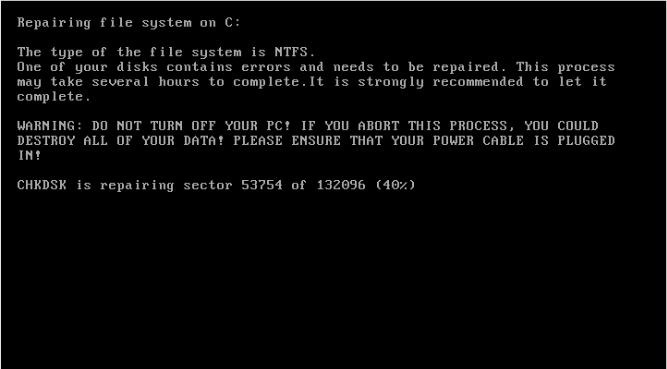
This screen is actually Petya scrambling your files. So the earlier you can stop the process by powering off, the more files that you will be able to recover.
I would also recommend that you immediately shut down all other machines that are on your network and seek technical support. By shutting down other machines that may be infected, but have not rebooted, you should not lose any of their data.
At this point you will need the assistance of your IT service provider to help recover the data.
I’m looking at this screen, what should I do?
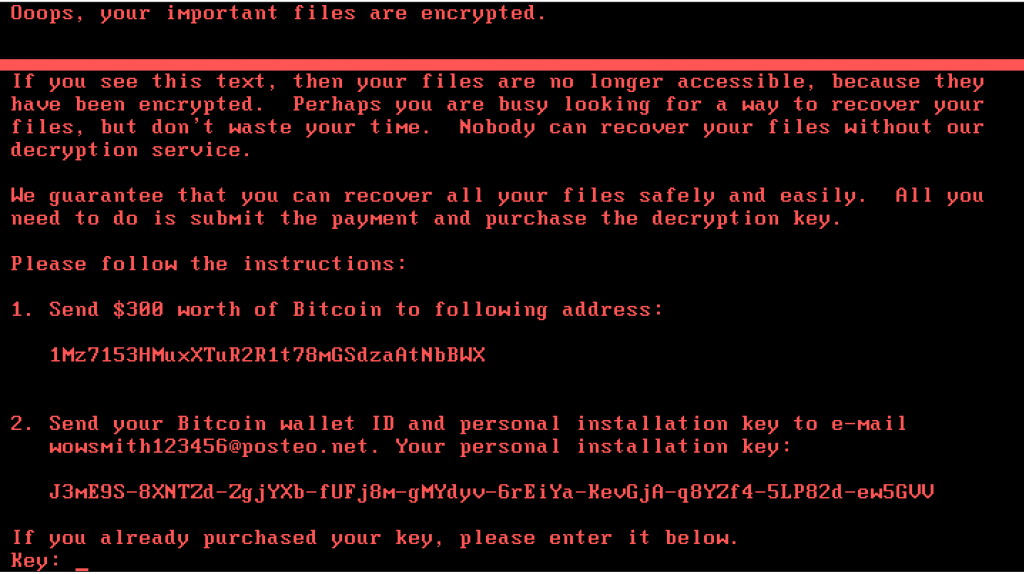
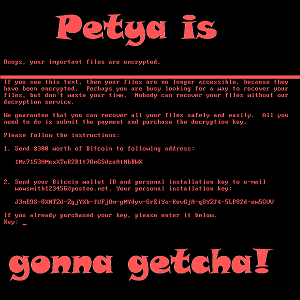
First things first – DON’T PAY! I’m not just saying that because it’s not a good idea to fund criminals, but because YOU WON’T get your files back. This is a purely destructive form of Ransomware.
If you need advice or assistance, please do not hesitate to contact us by e-mail at support@L2CyberSecurity.com.
Keep an eye on our Facebook and Twitter for updates, as and when significant changes happen.
