Dodgy e-mail that looks legit.
 I received a dodgy e-mail on my personal account yesterday. I’m surprised the GMail spam filters didn’t catch it and flag it for me. Like last weeks story, this message looked kinda plausible.It was a typical UPS delivery notification scam, which the evil doers spew out tens of thousands of and expect at least one person to be waiting on a delivery to fall for it.
I received a dodgy e-mail on my personal account yesterday. I’m surprised the GMail spam filters didn’t catch it and flag it for me. Like last weeks story, this message looked kinda plausible.It was a typical UPS delivery notification scam, which the evil doers spew out tens of thousands of and expect at least one person to be waiting on a delivery to fall for it.
Here is the offending dodgy e-mail:
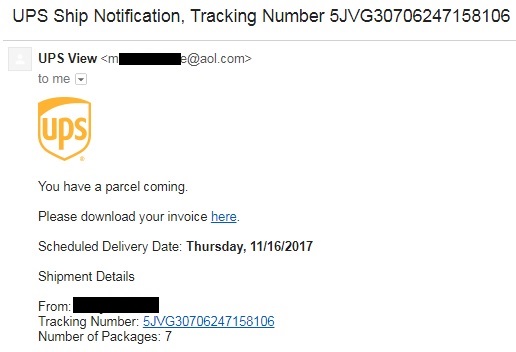
To me, there are a number of obvious indicators that this is a dodgy e-mail:
- The sending address (the bit after “UPS View”) was not a UPS address.
- The two links in the e-mail did not go to a UPS website.
- Most obviously … I wasn’t expecting a delivery!
So lets take them one at a time:
- Some e-mail clients don’t actually show you the whole e-mail address of the sender. They just show the Display Name, which in this case is “UPS View”. So if you were using such a client, then it would appear to be a legitimate UPS e-mail address. However in my case, there was this @aol.com e-mail address, which is not associated with UPS.
- When you see a link in an e-mail or website, you can hover the mouse over it. Somewhere towards the bottom of your browser window, you should be able to see where the link is going to take you. In this e-mail’s case it was going here, which is not a UPS site:
![]()
- In my case I wasn’t expecting any delivery. But what if I was? What if I was an under pressure procurement clerk in a large organisation? I’d be getting deliveries on a regular basis. I’d be very inclined to click on those links.
Please note I carried out the following action on a sacrificial machine, so please do not be tempted to ever click on links to see what happens next. It could end very badly for you.
So what would have happened if I did click on the link? A word document, with a name that started “Tracking-3154631…” was downloaded. This document, if opened, would persuade me to click on “Enable Editing” and then click on “Enable Content”. Once I had taken those actions, macros (a set of instructions for a computer) in the word document would have downloaded a really nasty piece of software. Then all of my files would have been scrambled and I would be presented with a ransom demand to get my data back.
If I was that under pressure procurement clerk, it would not have stopped at just the files on my computer, but any files that I could access on the company’s network. That could be very, very disruptive to the organisation.
Out of curiosity, I checked the website (the bit before the “/UPS/16-Nov….”) that hosted that document. It appears to be a legitimate business website. However, they’ve probably been hacked by the bad guys, who are now using their site to host their malicious downloads.
UPS offer advice on fraudulent e-mails.
As usual, we’ve even got a commandment that covers dodgy e-mails too. So have a read to see what you can do to protect yourself.
