Posts Tagged ‘Commandments’
The latest Ransomware outbreak – Petya
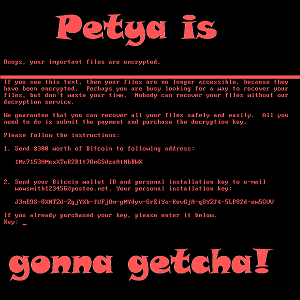
So here we go again with another outbreak of Ransomware, based on the National Security Agency (NSA) hacking tools that were leaked by a hacking group. Some experts are calling this one Petya, as it seems very similar to the Petya Ransomware strain that has been around for over a year.
Read MorePermission to spy on you?
Most people have smart phones these days and of course smart phones really come into their own through the use of Apps. There seems to be an app for every conceivable thing and lots of them are free. The phone makers make a good effort to protect us from bad apps by making sure that…
Read MorePhone scams – some current examples
In the last few days, I’ve received a couple of attempted phone scams. The first was a new one on me, but the second was an old favourite.
Read MoreSick subtitles can infect your media player
Do you use a media player like VLC, Kodi, Popcorn Time or Strem.io? Perhaps you are using one of those “dodgy” Android boxes? If so you will want to update them to their latest version ASAP because it is possible that they might pick up subtitles that can compromise the machine that you are playing…
Read MoreWannaCry no more. At least for now.
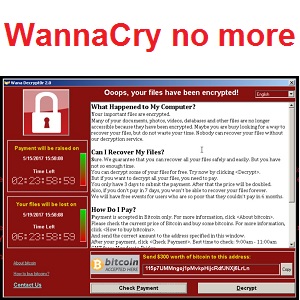
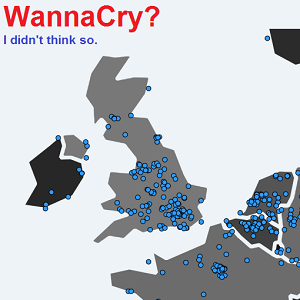
I’m just going to have a short article this week, just to close off the WannaCry story and counter any of the misinformation that was spread by some supposed “experts”. WannaCry is still circulating and affecting machines, but thanks to the kill switch discovered by @MalwareTechBlog, it is more or less neutralised now. Those machines still…
Read MoreDo you WannaCry? I didn’t think so.
I delayed this week’s blog, just to let some of the dust settle on the whole WannaCry (also known as WCry or WannaCrypt) furore and see if we can learn anything from it that will help protect my readers going forward. I’ll start with some easy background on Ransomware and them explain what was special…
Read MoreHackers released NSA hacking tools … World continues to turn ?.
You probably missed it – but don’t worry, I’m here to give you the simple low-down ?. The Cyber Security world was in meltdown for some of last weekend about the fact that a hacking group known as Shadow Brokers had released a load of NSA hacking tools to the internet and this meant everyone was…
Read MoreReally – Don’t open that Word attachment! It is malware.
It was reported over last weekend that there was a Microsoft Word vulnerability that allowed a type of Word malware (malicious software) to infect a persons PC/Laptop simply by opening the document. Even having macros disabled would not protect the victim. So what happens?
Read MoreEvil e-mail has your name and address!
Reports today are somewhat concerning. Below are two examples of evil e-mail that has been doing the rounds in the last day or so. The greeting addresses you by your first/given name and the file that is attached to the e-mail is called after your surname. The postal address shown IS also your address. I’ll…
Read MoreScary new way to have your GMail password and account stolen.
This is an incredibly easy way for the evil doers to steal your GMail ID and GMail password. This one could even catch out security people like me! ? So what happens is you receive an e-mail from somebody you know, who also had a GMail (note the emphasis on had).
Read MoreThere is a lot of variations in scam e-mail the last couple of days.
I yearn for the days when evil e-mail was so easily identified “becuse it wuz ritten in, gud, inglish wit grate spellhng an pun.tation”. ? In the last couple of days, the evil doers have been varying their scam e-mails fairly wildly and it’s bound to catch out some people. I’ll run through three sneaky methods…
Read MoreHere is a worrying aspect of the Yahoo breach.
Everyone has heard about the personal information related to 500 million Yahoo accounts being stolen from Yahoo in 2014. There’s lots of helpful tips out there (and some here too), but some people may not realise that they have a Yahoo account. Yahoo provides e-mail services to some big internet service providers (ISPs), over in…
Read MoreSnail mail delivers USB keys … WTF?
I find I’m writing a second article about Evil USBs within a week. At least these ones don’t destroy your equipment, but they might infect you with nasty software that does things that you really wouldn’t want it doing. In this case, in Victoria, Australia, Evil Doers were dropping USB drives into people’s mailboxes. The…
Read MoreA desktop/laptop killing USB device is on sale for €50.
As I’d mentioned in the detail section of a previous blog post there was a prototype USB memory stick that is designed to fry the electronics on a laptop or desktop, the instant it gets plugged into it. Well it’s now something you can buy for as little as €50. The worrying thing is, as…
Read MoreProtect your on-line accounts, but not with text messages.
As I outlined here, if you are using on-line accounts for e-mail, social media, etc. then one of the strongest means of protecting yourself from the evil doers is to use, what is called, two factor authentication. If you are not doing this now, you really should be as it improves your protection massively. This is…
Read More