Cyber Security for Charities
In today’s digital landscape, charities face increasing cyber threats that can compromise sensitive data and damage their reputation. Safeguarding your organisation’s information is crucial to maintaining trust and ensuring the continuity of your charitable work.
Read MoreCyber Security for Small Business
In today’s connected world, small businesses are increasingly vulnerable to cyber threats. Protecting your business from potential breaches and data leaks is essential for maintaining trust and safeguarding your reputation.
Read MoreIT Task Calendar for Small and Medium Businesses
If you are a small or medium business owner without an internal IT person or department, you should set up a schedule for performing some simple IT tasks. An IT Task Calendar if you will. This will make sure your IT is working well and everything is being kept up-to-date.
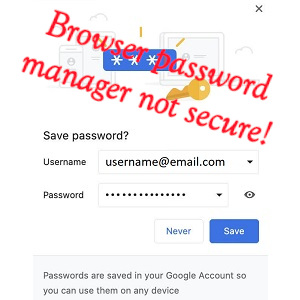
Read MoreBrowser Password Manager is not as secure as you think
Whenever I talk about password managers I often get asked by people about their browser password manager and whether that is a secure method of storing passwords. They’re not really the best solution. Here’s why.
Read MoreLegal Basis for Processing
The General Data Protection Regulation (GDPR) outlines the conditions under which there is a legal basis for processing personal data. Download Detailed Guidance Here Legal Basis for Processing: Articles 6 through 10 of the GDPR outline the various legal bases for processing along with specific conditions around things like consent, children’s data, sensitive data and…
Read MorePrinciples of the GDPR
The General Data Protection Regulation (GDPR) sets out the principles of the GDPR that organisations must follow when processing personal data. Download Detailed Guidance Here Principles of the GDPR: The GDPR outlines the basic rules for how companies should handle and protect people’s personal information: Lawfulness, fairness, and transparency: Organisations must process personal data…
Read MoreRights of an Individual
The General Data Protection Regulation (GDPR) provides strong rights of an individual, whose personal data is being processed by organisations. Download Detailed Guidance Here Rights of an individual: The right to be informed The right to be informed covers your responsibility to provide “fair processing information”, normally by way of a privacy notice. You need…
Read MoreAn Post Scam Email Gaeilge Edition
I know many people I talk to mention they have received An Post scam messages. These have increased dramatically in the last couple of years. Thank you Brexit! Over the weekend I received a new twist on it. An An Post scam email that was as Gaeilge (in Irish).
Read MoreBank account has changed – Scam alert!
If you hear or read the words “My bank account has changed.” you need to be on your guard. This is a massive red flag and is a fairly good indication that somebody is about to try to scam you.
Read More#WeekendWisdom 100 Something Completely Different
Welcome to #WeekendWisdom number 100. And now for something completely different.
Read More#WeekendWisdom 099 Using the security.txt file
Welcome to #WeekendWisdom number 99. This week we’re going to talk about using the security.txt file.
Read More#WeekendWisdom 098 Lessons from the Facebook Outage
Welcome to #WeekendWisdom number 98. This week we’re going to talk about Lessons from the Facebook Outage.
Read More#WeekendWisdom 097 Record Number of Zero Days
Welcome to #WeekendWisdom number 97. This week we’re going to talk about record number of zero days.
Read More