#WeekendWisdom 042 Consent Phishing
Welcome to #WeekendWisdom number 42. This week we’re going to talk about Consent Phishing.
What is consent phishing?
“What is consent phishing?” I hear you ask. It’s actually even a fairly new term even for me. Earlier this week, SANS the well-respected Cyber Security organisation revealed that they had had a data breach back in July. They detected it in August and they shared the results of their investigation with the public earlier this week.
What happened to them?
What had happened was, a number of their staff received the following email which looks like a genuine Office 365 file sharing email. One user fell for the phish and they clicked the Open button.
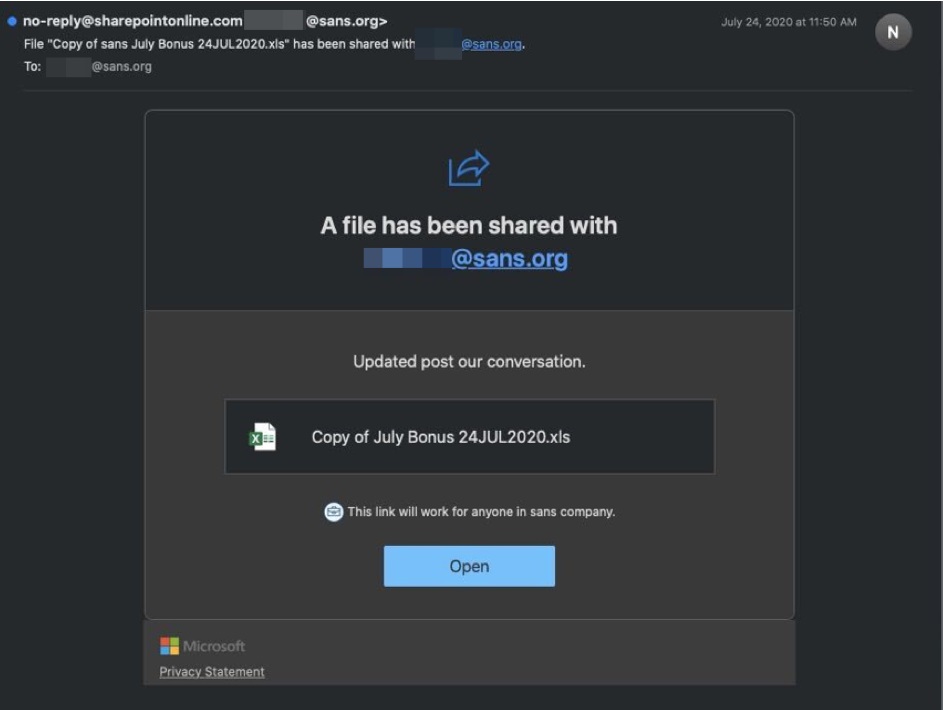
What happened then was a malicious Office 365 App tries to install. When it does that it needs to get permission. The user got popped up something similar to the following message to say “Can you give me permissions to do some of these things?”
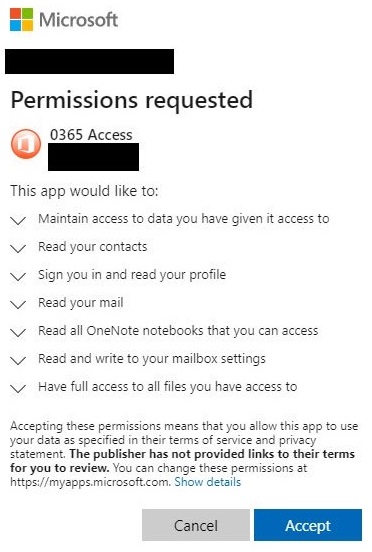
The user fell for that and they gave their permission. Then the app installed a forwarding rule on the user’s email account such that if any email containing the words:
- invoice
- payment
- bank
- BIC
- IBAN
- SWIFT
- account
all these type of financial terms. The rule will forward that email to an external address which is controlled by the hackers.
What should I look out for?
So if you ever get something that pops up unexpectedly looking to get permissions, to your Office 365 or G Suite accounts, stop and think, “Is this legitimate or not?”
So that’s it for this week. Let’s be careful out there and we’ll talk to you again next week.
How can L2 Cyber Security help you?
We offer a full range of training programmes, which can be delivered online or in-person*. We include these types of real world examples in our training, so people get to see what is actually tried by the criminals.
L2 Cyber Security are also a partner of CyberRiskAware for online self-directed Cyber Security Awareness training and Phishing testing.
Contact us for more information at info@L2CyberSecurity.com.
*With appropriate social distancing and other health and safety measures adhered to.
Follow us on Social media:
Liam is available on Twitter, LinkedIn and Instagram.
Follow L2 Cyber on Twitter, LinkedIn, Instagram and Facebook.
