Luas Ransomware Incident – Offline a while now
 How did you hear about the Luas Ransomware incident? Was it on the news? Online? Facebook? Twitter? Instagram? Or did you happen to visit the website to check some fare information and get confronted by a very basic ransom demand. Whatever way you found out about it, it happened over 40 hours ago and the website is still unavailable. They say that some 3,226 user records may have been compromised in this attack. They have now been contacted and the Data Protection Commission have been notified.
How did you hear about the Luas Ransomware incident? Was it on the news? Online? Facebook? Twitter? Instagram? Or did you happen to visit the website to check some fare information and get confronted by a very basic ransom demand. Whatever way you found out about it, it happened over 40 hours ago and the website is still unavailable. They say that some 3,226 user records may have been compromised in this attack. They have now been contacted and the Data Protection Commission have been notified.
They claim that their Standard Fare Notices and Tax Saver Ticket pages are not affected and are still available. I wonder about this, as I went to the version of their website from last December and there is no other part of the site there that records personal data. So the data breached must be belonging to those types of people. We’ll hear soon enough about this. It’s not what I want to focus on.
The site has been down for a long time.
For a company as large as Transdev is, I’m surprised at how long the home page for their major operation in Ireland has been unavailable. If they were following best practice, then this is, at a high-level, what should have happened on Wednesday night last:
- Ransomware compromises the web site.
- IT team become aware – incident response effort commences – server, web and security teams scrambled.
- Server(s) disconnected from all networks by physically pulling the network connectors out of the server(s), but they are left powered on.
- Security team take a forensic snapshot of the affected server’s memory and disk. This is a long slow process.
- Server team, bring up backup server or request a new server from service provider.
- Web team commence restore of the website from most recent backup on that server. Tests that all the pages work.
- Replacement server(s) put into production – website back online.
- Once the security team have completed their snapshots of the affected servers, these machines can be wiped and put to use again.
- Security team analyse the forensic images to discover source of the compromise and any loss of data. This process could take days and even weeks.
Given that the Luas site is pretty basic, step 7 above should easily have been achievable, I think, within 24 hours. Probably even faster if they had a backup server on stand-by, ready to take the restore.
Why is it taking so long?
I’m going out on a limb here. I’m guessing that they don’t have decent backups of their website. If they don’t have that, then they literally have to rebuild it from scratch and this will take time. Probably days.
Perhaps they thought they did have backups, but here’s the thing. You actually should test your backups occasionally to see if they are working OK. If they never tested that these backups work, they may have discovered that they weren’t backing up enough and they are going to have to rebuild it from scratch.
With good, tested backups this would not take much time at all.
How did the Luas Ransomware get in?
That’s a good question. We may never find out, but the likely cause is that they had a poorly secured website or webserver. It looks like they use WordPress and if you have a very old version of that, then it is trivial for a hacker to compromise it. The message from the bad guys was interesting:
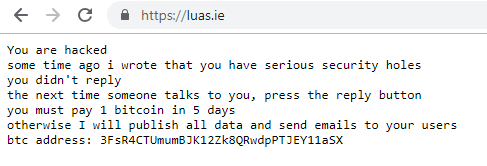
This person states that he warned the company some time ago that they had vulnerabilities and they never responded. This could be a complete lie, but it’s also quite possibly true.
Based on the wording of the message above, if I received a similarly worded e-mail, warning me about something wrong on my website, I might dismiss that too. However, I take my website security seriously and keep it updated on a weekly basis. I also back it up daily and finally, I have tested those backups.
What can you do to avoid such a long outage?
You don’t want to be affected by something like the Luas Ransomware do you?
There’s some simple steps that you can take. Basically keep your website updated regularly and have good backups which get tested. There are more, but these two will give you a quick win.
You could also give us a call on 087-436-2675 or drop a line to info@L2CyberSecurity.com and we can have a chat about the service that I can provide. We also have some Cyber Security training coming up soon too, which you can book a place on.
Lets be careful out there.
#SecuritySimplified #GDPR
