Data Breaches Everywhere
 It’s beginning to look a lot like Christmas … has come early for the evil doers. There just seems to be a relentless tale of data breach after data breach in recent weeks and it has been really bad in the last week. It really does look there’s data breaches everywhere you look. The worry about this, is that people may just think that this is the new normal and put up with it.
It’s beginning to look a lot like Christmas … has come early for the evil doers. There just seems to be a relentless tale of data breach after data breach in recent weeks and it has been really bad in the last week. It really does look there’s data breaches everywhere you look. The worry about this, is that people may just think that this is the new normal and put up with it.
Updated 05/12/18: To include the Dell, potential breach.
Last Wednesday, Dell announced a potential cybersecurity incident. This was followed on Friday when it was revealed that Marriott International Hotels had a massive 500m records stolen. These were all forgotten by Monday for most normal people and then later on Monday Quora, an online question and answer forum had 100m records stolen. A couple of weeks ago, Amazon notified an unknown number of customers that their name and e-mail address were exposed. Earlier in the month, VisionDirect in the UK had lost payment card data for an undisclosed number of customers.
That’s just 5 companies that you probably have heard of. I covered the NUI Galway breach separately a couple of weeks ago. There were lots more breached last month. I’ll give a synopsis on each one of the five and then discuss what can happen.
Quora have some questions to answer
So Quora had ~100m records accessed by persons unknown. They detected the issue on Friday 30th November and on Monday 3rd December they endeavoured to contain the issue. They logged out the impacted individuals and forced them to reset their passwords when they log back in. What was taken by the bad guys?
-
Account information, e.g. name, email address, encrypted (hashed) password, data imported from linked networks when authorized by users
-
Public content and actions, e.g. questions, answers, comments, upvotes
-
Non-public content and actions, e.g. answer requests, downvotes, direct messages
They claim not many subscribers used the direct messages features, so really the most important items lost here was the account information.
Marriott reserve second place in the data breach tables
I actually missed this story on Friday the 30th November, as I had promised a customer a security assessment report by the end of the week. So I stayed off social media for the day, while I completed it. There were a LOT of tweets to get through that night! ? This is currently the second biggest data breach in history after Yahoo!’s almost impossible to match record breaking 3 billion accounts breach as revealed in October 2017. So what did Marriott lose? The contents of the Starwood guest reservation database, going back as far as 2014, containing:
-
For approximately 327 million of these guests, the information includes some combination of name, mailing address, phone number, email address, passport number, Starwood Preferred Guest (“SPG”) account information, date of birth, gender, arrival and departure information, reservation date, and communication preferences.
-
For some, the information also includes payment card numbers and payment card expiration dates, but the payment card numbers were encrypted using Advanced Encryption Standard encryption (AES-128). There are two components needed to decrypt the payment card numbers, and at this point, Marriott has not been able to rule out the possibility that both were taken.
-
For the remaining guests, the information was limited to name and sometimes other data such as mailing address, email address, or other information.
Some of the data lost is genuinely concerning. Particularly the payment card information.
Bad guys try to ding dong Dell
This may or may not have been a breach. Dell haven’t given away too much information. Their security measures detected unauthorised activity that was …
… attempting to extract Dell.com customer information, which was limited to names, email addresses and hashed passwords.
Dell couldn’t say at this point whether these details were actually extracted from their systems by the bad guys. But even if they were unsuccessful in taking data, this just demonstrates that even massive companies like Dell can be broken into. Massive companies like … ⬇⬇⬇
Prime example of poor communication from Amazon
The Amazon data breach on 21st November doesn’t seem too bad. All that might have been compromised was name and e-mail address. However their notification to affected customers was pretty poor.
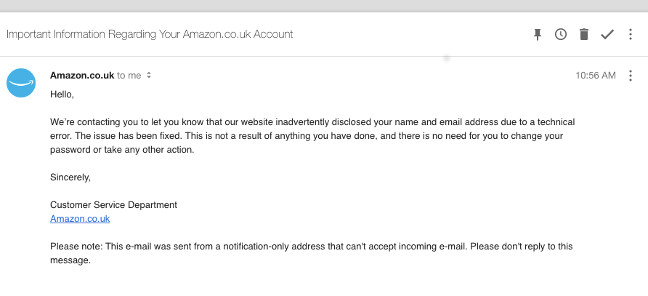
A lot of security professionals have said that this looks very “scammy”. While I would tend to agree as it’s very light on any details, there’s no suggestion that the recipient should take some urgent action. If that had been the case, I would fully agree.
Is there short-sighted security in place at VisionDirect?
Back on the 19th November, VisionDirect in the UK issued a statement about a data breach. The breach affected customers who updated their details or placed orders between the 3rd November and 8th November. What data was accessed by the evil doers?
The personal information was compromised when it was being entered into the site and includes full name, billing address, email address, password, telephone number and payment card information, including card number, expiry date and CVV.
In fairness to them, they were very specific about the timeframe when the website was compromised. “Between 12.11am GMT 3rd November 2018 and 12.52pm GMT 8th November 2018.” This was repeated ad nauseam.
What can happen when there are data breaches everywhere?
A common feature of all the above breaches are names and email addresses. While you might not think these are worth anything, 50,000 valid email addresses can be sold for up to $50 on criminal exchanges on the “dark web”. I hate that term by the way. It’s so “hackery”. Anyway, your email address has a small, but material value.
Payment card data is the next thing that is of immediate value, particularly where the bad guys have the CVV/3 digit security number. These can be immediately put to work purchasing vouchers which are then immediately spent. The card numbers are also valuable on their own and sell for up to $60 each. While Marriott had the credit card numbers encrypted, they were not sure if the required information to decrypt them again was also exposed. So I would assume that it was.
Passwords are the next concern. Quora had “hashed” passwords which is good. These are hard (but not impossible) to crack. They also forced a password reset on affected subscribers, so that’s another mitigation. With VisionDirect, the password was totally compromised. This is because it was captured when a user was signing on to the site. They forced password changes on people who were impacted. However, if the password is used on ANY other account, particularly email, banking and social media, then you must change them all.
The rest of the data that was breached is still incredibly useful to the criminals. In particular from the Marriott breach. They have reservation details, probably into the future. So they know the future likely movements of people. They have loyalty card information, which, along with other data points, can be used to compromise a person’s Starwood’s Preferred Guest account and re-direct the rewards elsewhere.
The amount of data leaked, over such a long time at Marriott is pretty bad. This can be merged with lots of other data breaches and the evil doers can build quite a profile on each individual. I’ve discussed before how breached data from multiple sources can be put to evil use.
Data breaches everywhere indeed.
How can we help?
As the saying goes, preparation is half the battle. If you’ve not prepared to handle a data breach, it will be a much bigger struggle. We can help you prepare, both for a breach and handling the aftermath.
If you want to discuss further, please call on 087-436-2675 or send an e-mail to info@L2CyberSecurity.com and somebody will get in touch. We will make it straightforward and easy for you to be ready for an incident.
Lets be careful out there.
#SecuritySimplified
#GDPR #SimpleGDPR
